
Academy
Author: daniboomberger Date: 21.12.2020
Enumeration
Of course we start with the usual enumeration part. First task we have to add academy.htb to the so called /etc/hosts file. I run gobuster to get some more directories/files that could be useful. After I usually run some automated scripts, I let them run in the background and enumerate the website.
Nmap && Gobuster
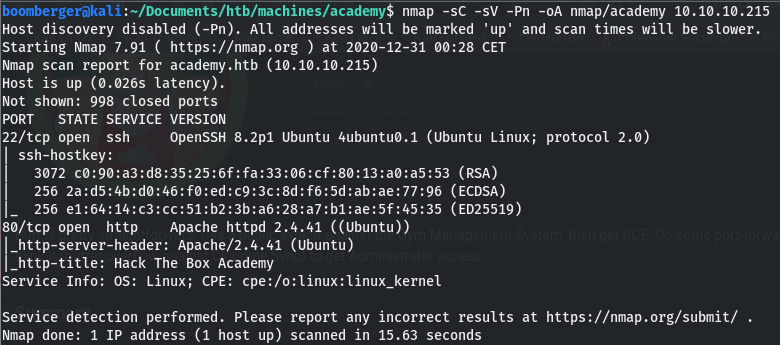
The Gobuster script actually found some directories, which I wouldn’t found just with the normal enumeration of the website.
Registration of admin account
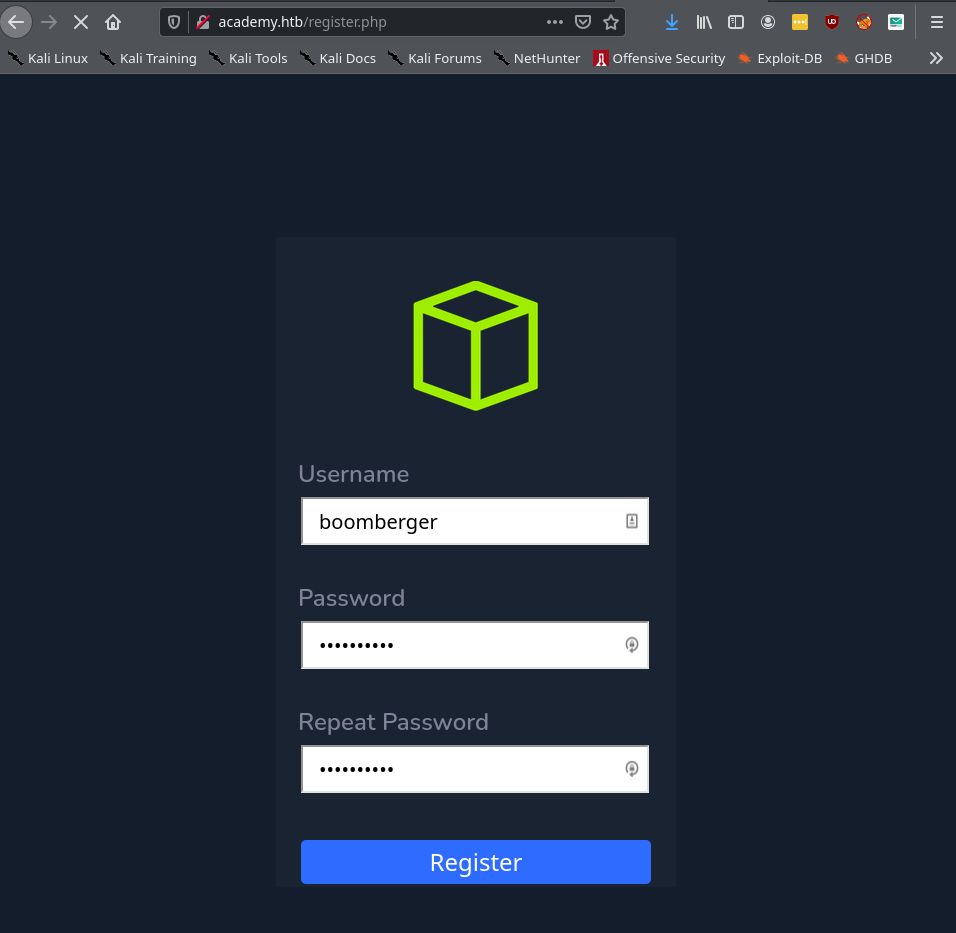
An another more interesting part of enumeration is the analyzing the traffic of some processes on the website. So what I do is run process as the registration as seen in the picture through burp and analyze parameters and find vulnerbilities or here a hidden parameter, which we can manipulate to gain a admin account.

As we see in the Picture above, there is a parameter which is interesting. The so called parameter roleid=0 is set to 0 by default. It would create a normal user account to the normal login page. So when we interceept the register.php we change the roleid= to 1 that creates an admin account.
Admin on the webpage

So after we can register a fully blown admin account for the website we try to login in the before found admin.php login site.
Subdomain (dev-staging-01.academy.htb)
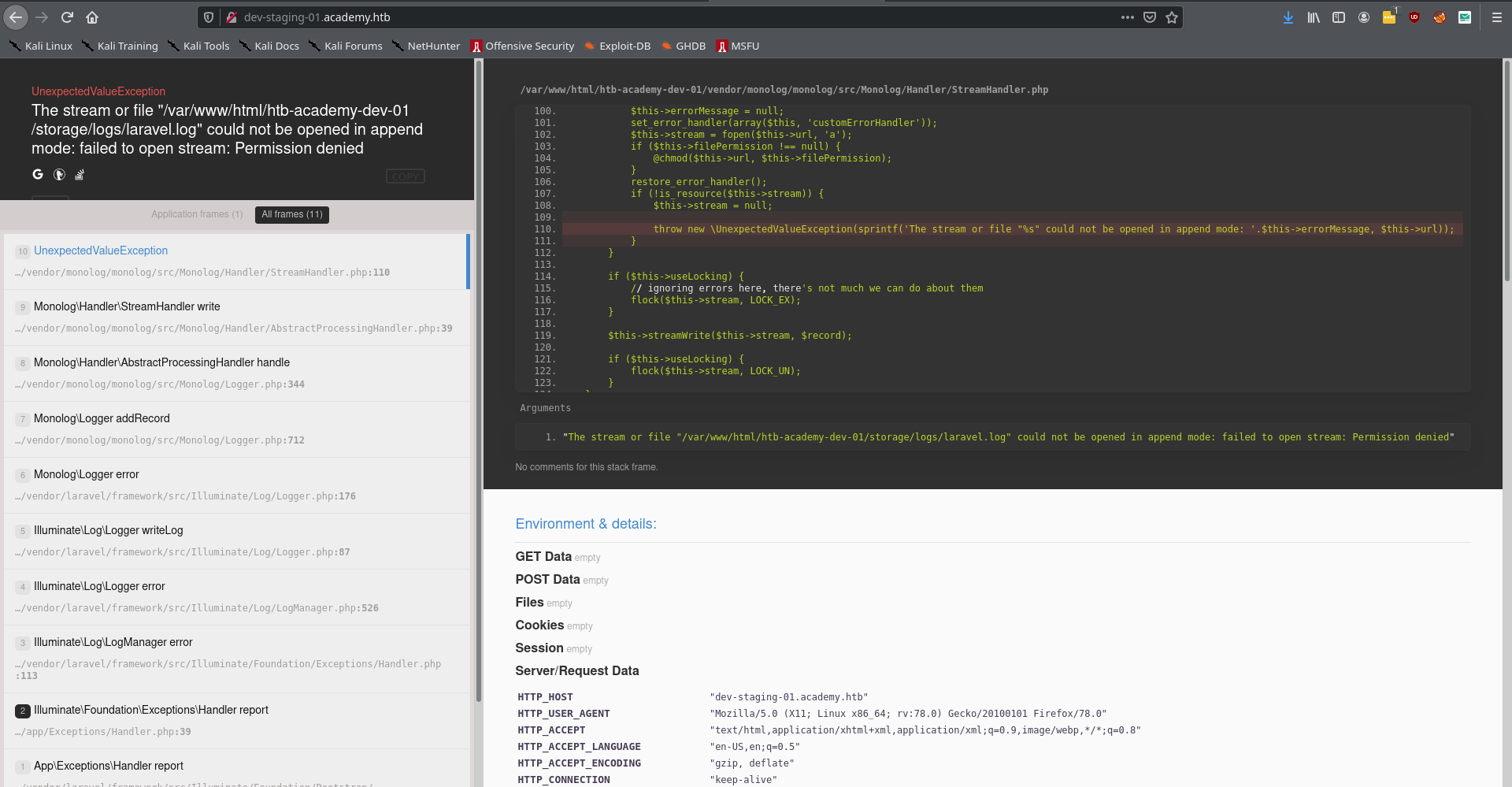
With some information found and a lot of research to find the exact exploit we find a Remote Code Execution for the laravel framework.
PHP Laravel Framework exploit
The screenshot shows us the usable laravel exploit. The Options to set are actually as usual in metasploit. The only problem you could have is if you forget to set the APP_KEY that can be found on the subdomain.
Enumerate on the machine
As usual on linux machine I run linpeas. It’s basicall my go to tool in linux boxes cause it provides me with a lot of information and can lead me to new path of elevating my privileges. We search for a way to get to antoher user so usually I look for interesting files to get credentials to reuse. In the .env file we find some reusable password. It leads us to ability to connect with ssh. Now we are the user cry0l1t3. From the user cry0l1t3 it takes a lateral movement to mrb3n to then official end the box with root. The Enumeration from cry0l1t3 is similar to the beginning we ran linpeas search for reusable passwords and look in the audit logs. Again after a lot of digging we find var/audit/logs and grep out the password for our next user mrb3n.
Root
Especially this root wasn’t hard because it was really straightforward. You just needed to run sudo -l as mrb3n and look at what binaries there are. We find composer is able to run as root and we research to get root with composer.
1
2
3
TF=$(mktemp -d)
echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
sudo composer --working-dir=$TF run-script x
Here we are root!!!!!
